40 azure information protection labels examples
How to Deploy a Secure FTP (SFTP) Service on Microsoft Azure 6) Connect using the public IP address and authenticate to the SFTP service using your favorite FTP/SFTP client (FileZilla) for example. Click on the "Deploy to Azure" button and follow the steps as shown in the video below to deploy the SFTP service with a new storage account and two Azure file shares, one for the SFTP data upload, and the ... docs.gitlab.com › ee › integrationUse Microsoft Azure as an authentication provider | GitLab To enable the Microsoft Azure OAuth 2.0 OmniAuth provider, you must register an Azure application and get a client ID and secret key. Sign in to the Azure portal. If you have multiple Azure Active Directory tenants, switch to the desired tenant. Note the tenant ID. Register an application and provide the following information:
Get started with trainable classifiers - Microsoft Purview (compliance ... Make sure the items in your seed set are strong examples of the category. The trainable classifier initially builds its model based on what you seed it with. The classifier assumes all seed samples are strong positives and has no way of knowing if a sample is a weak or negative match to the category.

Azure information protection labels examples
Sources and sinks | Cloud Storage Transfer Service Documentation ... The table below details the supported sources and destinations. Cloud Storage is a valid sink for transfers from all sources. Transfers from Cloud Storage, Amazon S3, and Azure to Cloud Storage do not require agents or agent pools; they are managed entirely by Storage Transfer Service. To configure Cloud Storage as a source and/or sink, refer ... Microsoft Azure sandbox issue in az upgrade when ml already exists ... Auto-Assign customer-reported Issues that are reported by GitHub users external to the Azure organization. CXP Attention This issue is handled by CXP team. Extensions `az extension` commands or extension infrastructure feature-request Machine Learning az ml Upgrade az upgrade Deploy Workload Clusters to Azure - VMware To deploy workload clusters to an alternative Azure Service Principal account, different from the one used to deploy their management cluster, do the following: Create the alternative Azure account. You use the details of this account to create an AzureClusterIdentity in a later step.
Azure information protection labels examples. 10 BEST Reporting Tools in 2022 For Better Decision Making #1) Zoho Analytics #2) HubSpot Marketing Analytics #3) Integrate.io #4) FineReport #5) Query.me #6) Answer Rocket #7) SAP Crystal Reports #8) Izenda Reports #9) DBxtra #10) Datadog #11) BIRT #12) KNIME #13) GoodData #14) Phocas #15) Microsoft Power BI #16) Whatagraph #17) Oribi #18) Juicebox Conclusion Recommended Reading Blogs - Microsoft Tech Community Labels. Select Label () Clear ... Defender Microsoft Defender for Endpoint Microsoft Endpoint Manager Microsoft Flow Microsoft Forms Microsoft Graph Microsoft Information Protection Microsoft Lists Microsoft Sentinel Microsoft Teams migration Mobile Mobile Application Management ... We continue to expand the Azure Marketplace ecosystem. For ... azure-sdk-for-python/README.md at main - GitHub Azure Identity client library for Python. The Azure Identity library provides Azure Active Directory (AAD) token authentication through a set of convenient TokenCredential implementations. It enables Azure SDK clients to authenticate with AAD, while also allowing other Python apps to authenticate with AAD work and school accounts, Microsoft ... Public preview of out-of-the-box trainable classifiers with auto ... With Microsoft Purview Information Protection, we are building a unified set of capabilities for data classification, labeling, and protection not only in Office apps but also in other popular productivity services where information resides (e.g. SharePoint Online, Exchange Online, and Microsoft Teams), as well as endpoint devices.
Secrets | Kubernetes For example: implement (or deploy) an operator that fetches short-lived session tokens from an external service, and then creates Secrets based on those short-lived session tokens. Pods running in your cluster can make use of the session tokens, and operator ensures they are valid. Microsoft Entra (Azure AD) - Microsoft Tech Community Labels. Azure Active Directory (AAD) 1,296. Identity Management 490. Access Management 348. Microsoft 365 320. Azure AD B2B 183. Azure AD Connect 47. azure ad 44. Conditional Access 40. Cognitive Speech Services Pricing | Microsoft Azure The acoustic model is a classifier that labels short fragments of audio into one of several phonemes, or sound units, in each language. These phonemes can then be stitched together to form words. For example, the word “speech” is comprised of four phonemes “s p iy ch”. These classifications are made on the order of 100 times per second. Customizing the acoustic model … Understanding Microsoft Information Protection Encryption … 17/03/2021 · Deploy Azure Information Protection in your organization, configure labels, policies. Deploy multiple RMS services within your AIP environment. Configure Azure RMS protection policies for “regular” sensitive data. Configure AD RMS protection policies for “sensitive” data. Keep your AD RMS out of demilitarized zone (DMZ). Configure RMS …
Azure SDK for .NET (August 2022) | Azure SDKs - GitHub Pages The automatic configuration to trust the service's TLS certificate in ConfidentialLedgerClient now checks that the final certificate in the server's certificate chain matches the trusted TLS certificate. Previously the client checked if the thumbprint of the trusted TLS certificate was present anywhere in the server's certificate chain. Monitoring and troubleshooting apps in Azure Functions Let's explore how to use Azure Functions diagnostics to diagnose and solve common function app issues. Navigate to your function app in the Azure portal. Select Diagnose and solve problems to open Azure Functions diagnostics. Once you're here, there are multiple ways to retrieve the information you're looking for. techcommunity.microsoft.com › t5 › securityMicrosoft Information Protection and Microsoft Azure Purview ... Dec 07, 2020 · Core to Microsoft Information Protection is its classification capabilities, like the built-in sensitive information types that enable you to detect sensitive information in your data estate. Examples of sensitive information include social security numbers, addresses, credit card numbers, and other personally identifiable information that are ... Microsoft Information Protection and Microsoft Azure Purview: … 07/12/2020 · Examples of sensitive information include social security numbers, addresses, credit card numbers, and other personally identifiable information that are mapped to various global regulations. Also core to MIP are sensitivity labels. Organizations create these sensitivity labels in the Microsoft 365 compliance center after considerable thought and cross-group …
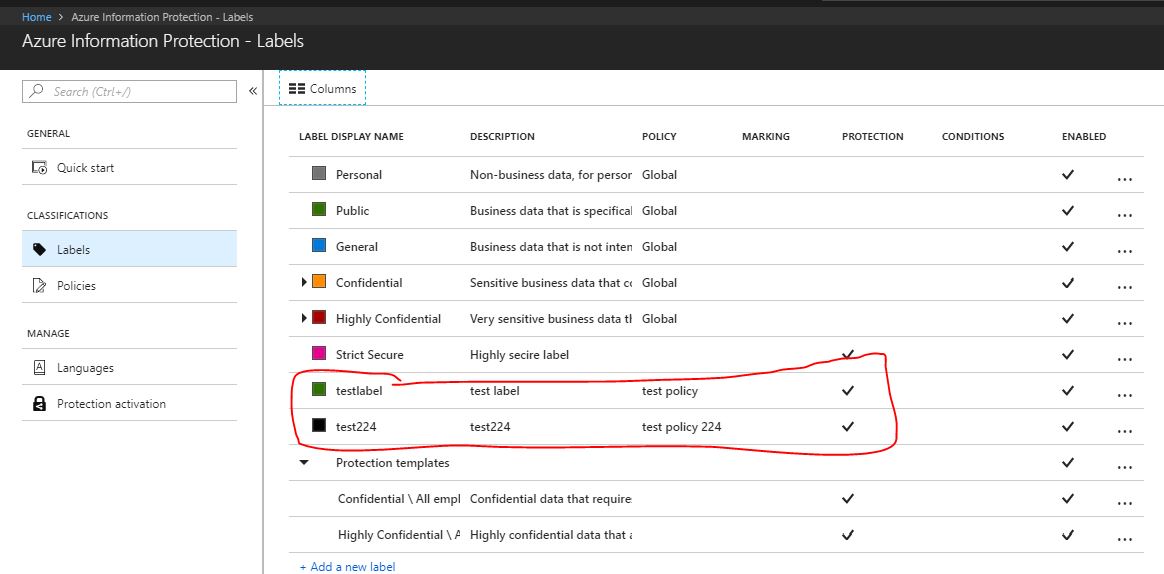
AIP Audit Export - Code Samples | Microsoft Learn To get started with the Azure Information Protection Analytics workbook, navigate to a log analytics workspace, select the workbooks tab, and create a new workbook. Select the Advanced Editor icon within the new workbook. Go to the AIPAnalyticsWorkbook.json file within GitHub and copy the contents.
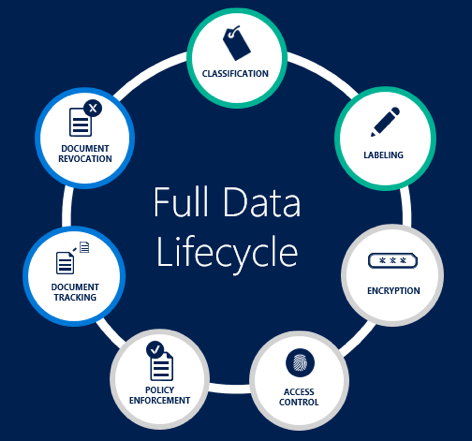
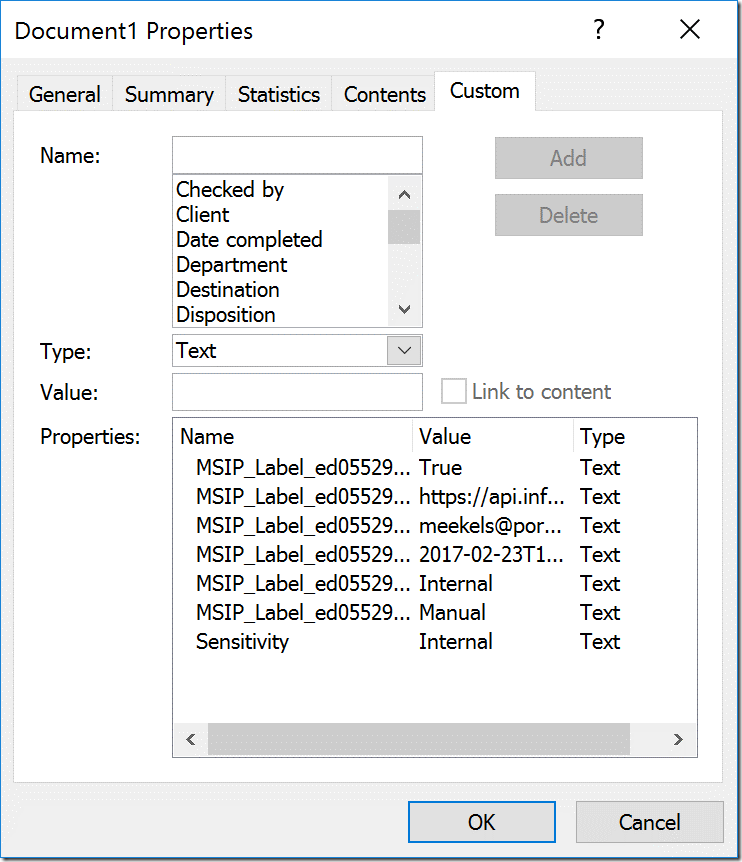
Microsoft Purview Information Protection - Microsoft Purview ... These include files in storage such as Azure Data Lake and Azure Files, and schematized data such as columns in Azure SQL DB, and Cosmos DB. Labeling in Microsoft Purview Data Map: Microsoft Information Protection SDK: Extends sensitivity labels to third-party apps and services. Example scenario: Set and get a sensitivity label (C++)
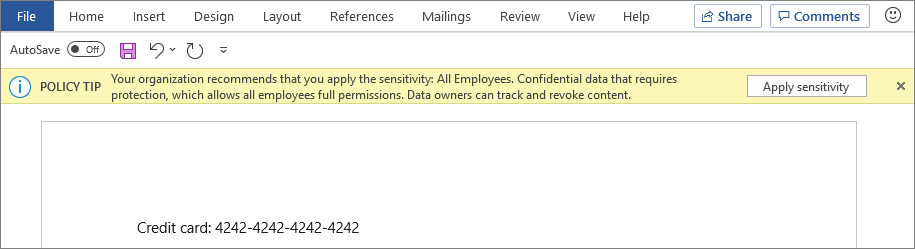
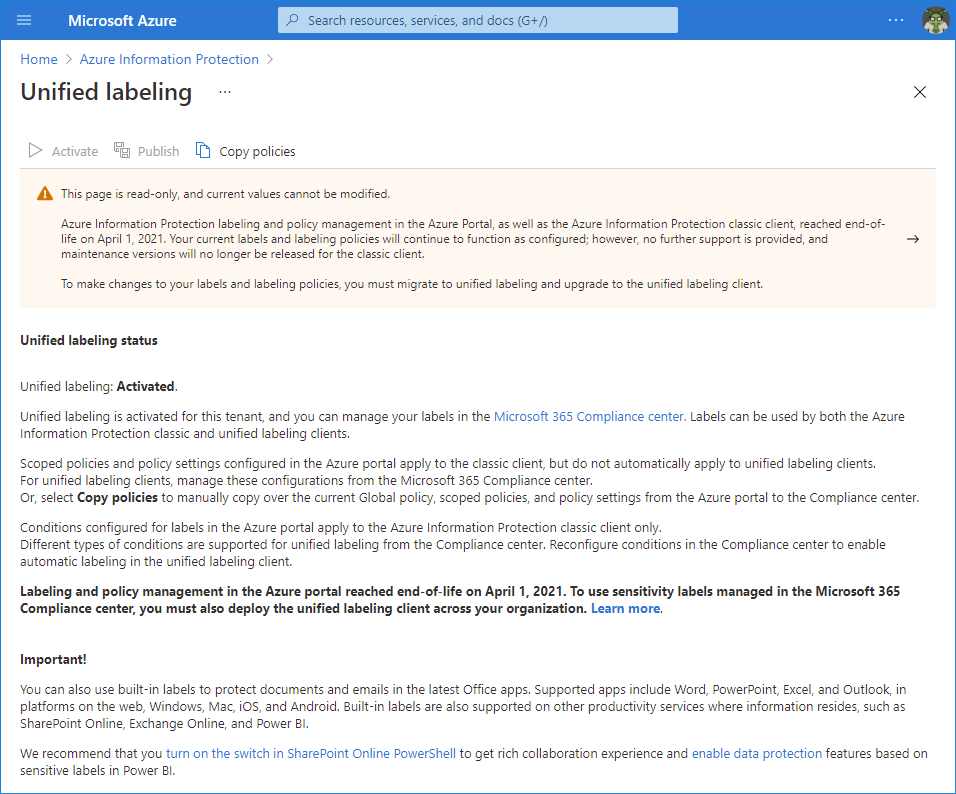
Azure Information Protection - Double Classification Dear All, We have applied Information protection labeling on all the users with default label as "Public". Seems the encryption, content marking are working fine. But somehow users are seeing double classification like below when they send email from mobile device to desktop app (Using Outlook).
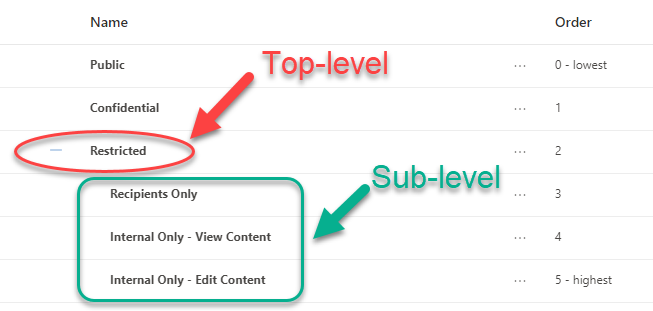
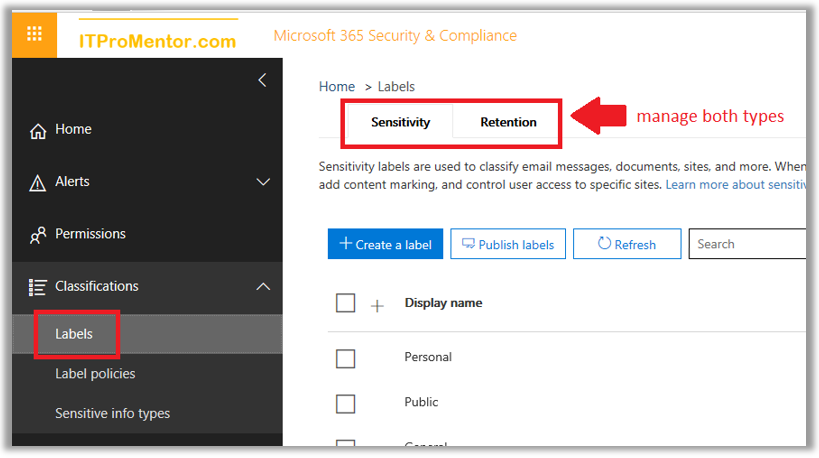
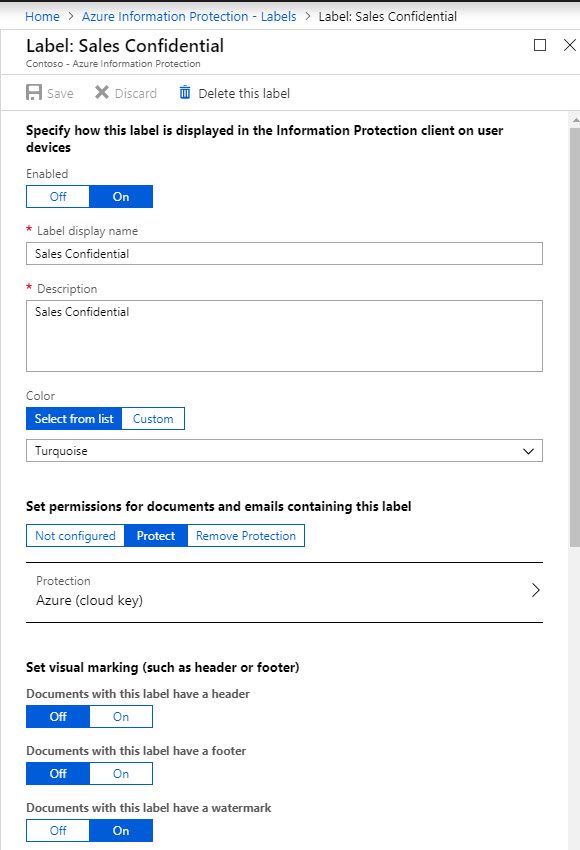
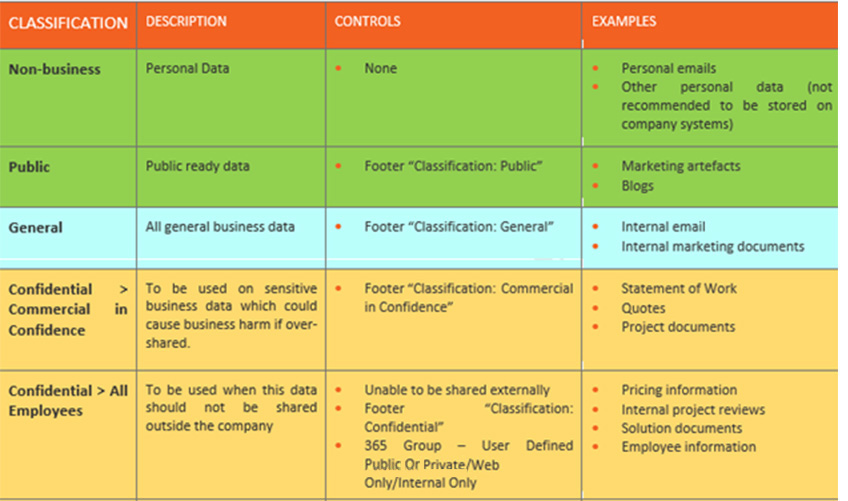
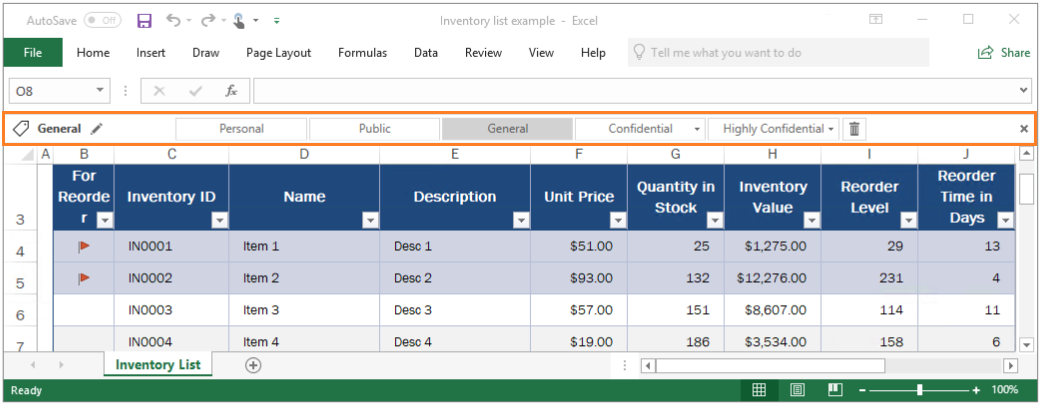
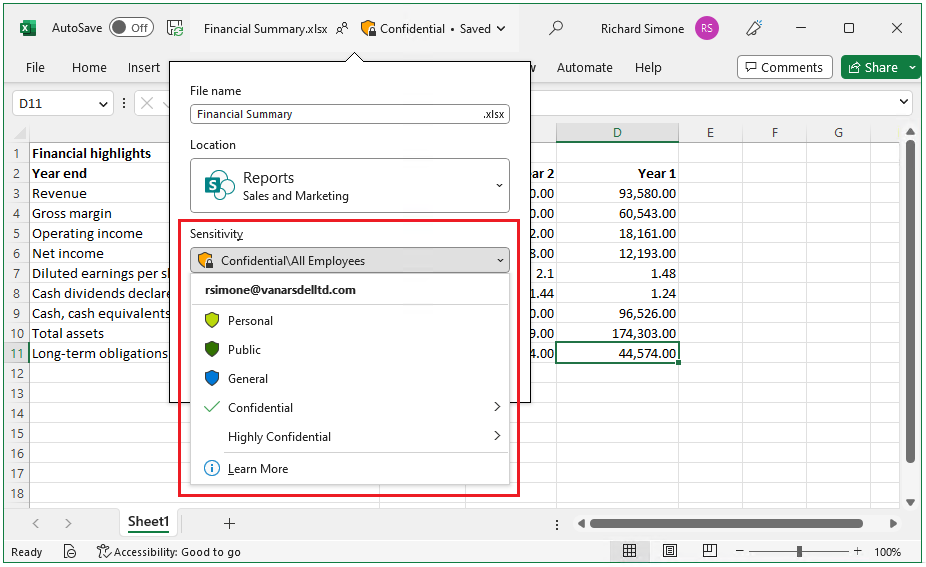
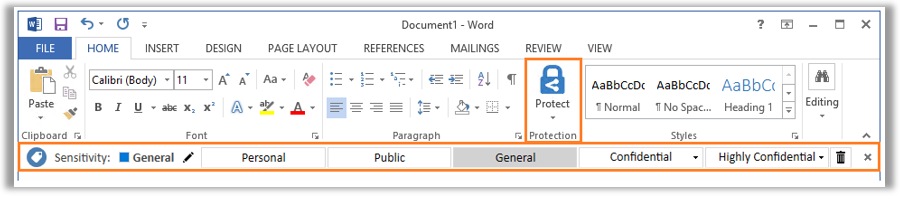
Get started with sensitivity labels - Microsoft Purview (compliance) Configure the protection settings you want associated with each label. For example, you might want lower sensitivity content (such as a "General" label) to have just a header or footer applied, while higher sensitivity content (such as a "Confidential" label) should have a watermark and encryption. Publish the labels.
AI Platform Data Labeling Service | Google Cloud For example, to train a model that can identify flowers in images, you must label objects like sunflowers, roses, and tulips in the image dataset. To train a model that can identify the names of...
Use Microsoft Azure as an authentication provider | GitLab To enable the Microsoft Azure OAuth 2.0 OmniAuth provider, you must register an Azure application and get a client ID and secret key. Sign in to the Azure portal. If you have multiple Azure Active Directory tenants, switch to the desired tenant. Note the tenant ID. Register an application and provide the following information:
Policies: Review Process | Azure SDKs - GitHub Pages Sample example Should be added to library's sample folder ( example) Quickstart samples Optional for introductory meeting See "Quickstart Samples" section below 2. API Review During API reviews, we look at sample code and detailed API listings. You can see an example of such listing here.
azure.microsoft.com › en-gb › pricingPricing - Microsoft Purview | Microsoft Azure Refer to the Managed Resources section in the Azure portal within Azure Purview Resource JSON. Note: Customers using Microsoft Purview to govern data in other clouds (example AWS, GCP) may incur additional charges due to data transfers and API calls associated with the publishing of meta-data into the Microsoft Purview Data Map.
FAQs for Azure Information Protection (AIP) | Microsoft Learn 17/08/2022 · If you are migrating your Azure Information Protection labels to the unified labeling store, ... For more information and some walk-through examples, see the following blog post: Conditional Access policies for Azure Information Protection. Additional information: Topic Details ; Evaluation frequency: For Windows computers, and the current preview …
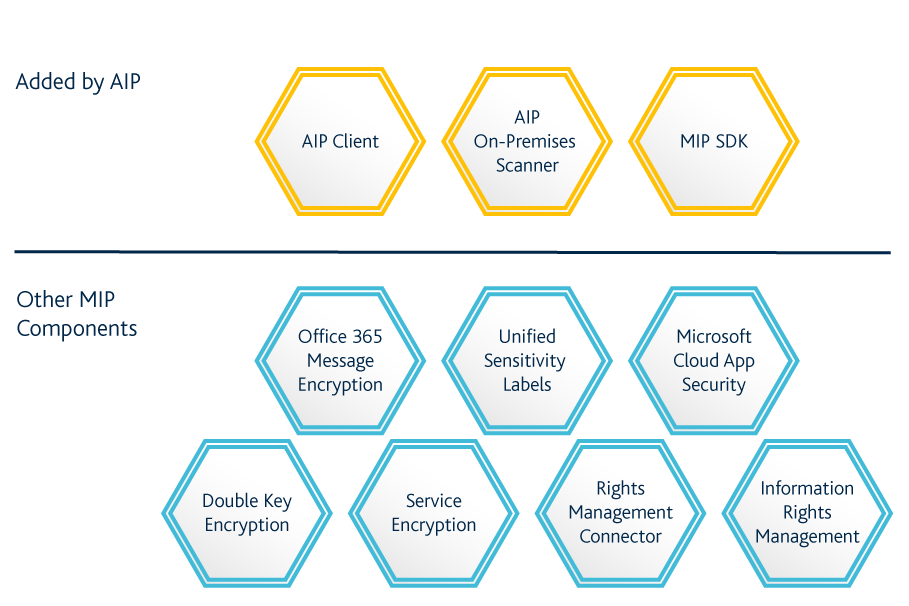
techcommunity.microsoft.com › t5 › securityUnderstanding Microsoft Information Protection Encryption Key ... Mar 17, 2021 · Microsoft stores one key in Microsoft Azure and the customer holds the other key. Customers maintain full control of one of your keys using the Double Key Encryption service. You can apply protection using the Azure Information Protection Unified Labeling client to your highly sensitive content. High Level Architecture of Double Key Encryption:
azure.microsoft.com › en-us › pricingCognitive Speech Services Pricing | Microsoft Azure The acoustic model is a classifier that labels short fragments of audio into one of several phonemes, or sound units, in each language. These phonemes can then be stitched together to form words. For example, the word “speech” is comprised of four phonemes “s p iy ch”.
Using IAM securely | IAM Documentation | Google Cloud Introduction. This page recommends security best practices that you should keep in mind when using IAM. This page is designed for users who are proficient with IAM. If you are just starting out with IAM, these instructions will not teach you how to use it; instead, new users should start with the IAM Quickstart.
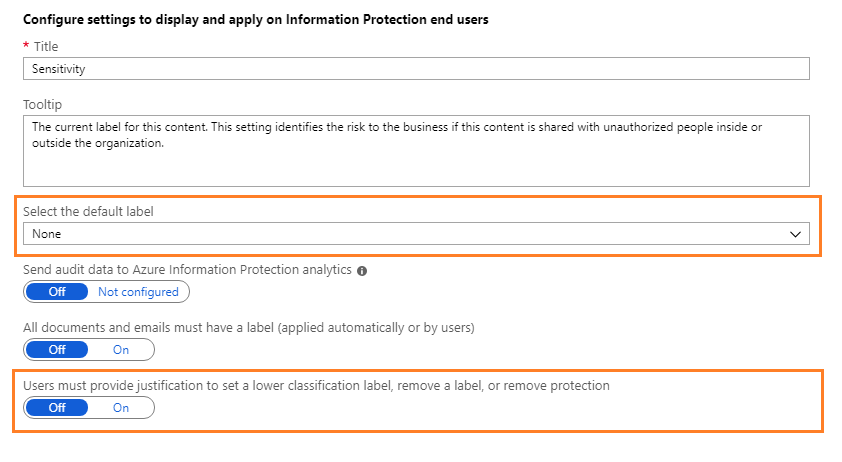
learn.microsoft.com › en-us › azurePrepare users and groups for Azure Information Protection Aug 01, 2022 · How users and groups are used by Azure Information Protection. There are three scenarios for using users and groups with Azure Information Protection: For assigning labels to users when you configure the Azure Information Protection policy so that labels can be applied to documents and emails. Only administrators can select these users and groups:
Implement these 6 Azure cost optimization best practices That said, there are some general strategies to reduce Azure costs. For example, an organization can tap into different payment plans, use native Azure cost management tools and rely on resource tags. Here are six Azure cost optimization best practices, several of which can apply to any Azure resource type. 1. Explore payment options.
Unified Data Governance with Microsoft Purview | Microsoft Azure Classify data using built-in and customised classifiers and Microsoft Information Protection sensitivity labels. Label sensitive data consistently across SQL Server, Azure, Microsoft 365, and Power BI. Easily integrate all your data catalogues and systems using Apache Atlas APIs. Learn more about Microsoft Purview Data Map
C++ Guidelines: Introduction | Azure SDKs - GitHub Pages For example, az is allowed since it is commonly used to mean Azure, and iot is used since it is a commonly understood industry term. However, using kv for Key Vault would not be allowed since kv is not commonly used to refer to Key Vault.
terraform-provider-azurerm/CHANGELOG.md at main - GitHub azurerm_data_protection_backup_policy_postgresql_resource - prevent a crash when given an empty criteria block azurerm_disk_encryption_set - prevent an issue during creation when the disk encryption set and key vault are in different subscriptions ( #17964 )
Azure-DataFactory/PrePostDeploymentScript.Ver2.ps1 at main - GitHub example: "testTrigger", "storageEventsTrigger" The script is not very comprehensive in detecting the trigger changes, so this parameter can be used to stop triggers explicitly if required #> param ( [ parameter ( Mandatory = $true )] [ String] $ArmTemplate, [ parameter ( Mandatory = $true )] [ String] $ResourceGroupName,
Azure.Default - PSRule for Azure - GitHub Pages The following rules are included within Azure.Default. This baseline includes a total of 304 rules. Name. Synopsis. Severity. Azure.ACR.AdminUser. Use Azure AD identities instead of using the registry admin user. Critical. Azure.ACR.ContainerScan.
Introduction to external data sources | BigQuery | Google Cloud These tables can be temporary or permanent. Permanent BigLake and external tables are contained inside a dataset, and you manage them in the same way that you manage a standard BigQuery table. For...
Apps on Azure - Microsoft Tech Community Get the latest updates on Azure products and features. Apps on Azure blog. Microsoft Customer Co-creation -. Share your thoughts and influence the outcome before a single line of code is written. Play an early role in product and service development by helping Microsoft build and test the features that you need in Cloud and AI services.
Office 365 License Comparison: Business Plans Vs. E5, E3 and E1 - Agile IT Building off the E1 and E3 business plans, Office 365 E5 is the highest tier Microsoft offers. With this license, you gain Audio Conferencing, Phone System, Power BI pro, Customer Lockbox, and Microsoft Cloud App Security: If you use or plan to use Skype for Business Cloud PBX, we recommend the Office 365 E5 license.
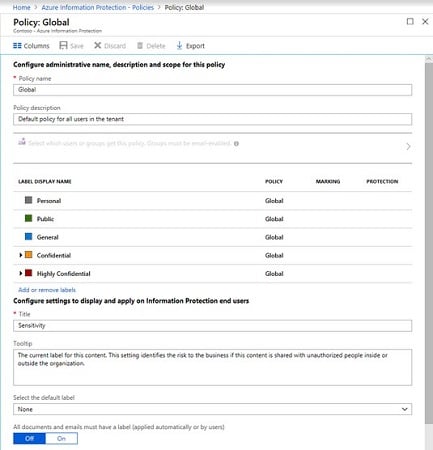
Prepare users and groups for Azure Information Protection 01/08/2022 · For assigning labels to users when you configure the Azure Information Protection policy so that labels can be applied to documents and emails. Only administrators can select these users and groups: The default Azure Information Protection policy is automatically assigned to all users in your tenant's Azure AD. However, you can also assign additional …
By pillar - PSRule for Azure - GitHub Pages PSRule for Azure includes the following rules across five pillars of the Microsoft Azure Well-Architected Framework. Cost Optimization Pricing and billing model Reports Resource usage Operational Excellence Automation Configuration Deployment Monitoring Principles Release engineering Repeatable infrastructure Tagging and resource naming
learn.microsoft.com › en-us › azureFAQs for Azure Information Protection (AIP) | Microsoft Learn Aug 17, 2022 · This Azure Active Directory administrator role enables administrators to configure Azure Information Protection in the Azure portal and some aspects of other Azure services. Administrators with this role cannot run any of the PowerShell cmdlets from the AIPService module , or track and revoke documents for users.
Deploy Workload Clusters to Azure - VMware To deploy workload clusters to an alternative Azure Service Principal account, different from the one used to deploy their management cluster, do the following: Create the alternative Azure account. You use the details of this account to create an AzureClusterIdentity in a later step.
Microsoft Azure sandbox issue in az upgrade when ml already exists ... Auto-Assign customer-reported Issues that are reported by GitHub users external to the Azure organization. CXP Attention This issue is handled by CXP team. Extensions `az extension` commands or extension infrastructure feature-request Machine Learning az ml Upgrade az upgrade
Sources and sinks | Cloud Storage Transfer Service Documentation ... The table below details the supported sources and destinations. Cloud Storage is a valid sink for transfers from all sources. Transfers from Cloud Storage, Amazon S3, and Azure to Cloud Storage do not require agents or agent pools; they are managed entirely by Storage Transfer Service. To configure Cloud Storage as a source and/or sink, refer ...







![Updated] Microsoft Information Protection Best Practices- Part 2](https://www.netwoven.com/wp-content/uploads/2021/08/MIP-02-1024x538.png)
















Post a Comment for "40 azure information protection labels examples"